How To Create A Virus Using C++ Pdf
What is Virus ?

Learn ethical-hacking - ethical-hacking tutorial - computer-viruses - ethical-hacking examples - ethical-hacking programs
- A program which will automatedly self-replicate by infecting other programs and files on your computer.
- The complication of this programs includes wiping your hard drive, displaying a joke in a small box, or doing nothing at all except to replicate itself.
- This type of infections tend to be localized to your computer and not have the ability to spread to another computer on their own.
History of virus
Learn ethical-hacking - ethical-hacking tutorial - virus-history - ethical-hacking examples - ethical-hacking programs
Types of viruses :
- There are variety of viruses available. Such as,
What is Boot Sector Virus

Learn ethical-hacking - ethical-hacking tutorial - boot-sector-virus - ethical-hacking examples - ethical-hacking programs
- Boot sector viruses infect either the
- master boot record of the hard disk
- external drives like floppy drive, Pen drives and other external hard disks.
- System boot impact - The boot record program responsible for the booting of operating system is replaced by the virus. The virus either copies the master boot program to another part of the hard disk or overwrites it.
- How this virus works : They infect a computer when it boots up or when it accesses the infected external memory disks such as pen driver or floppy disk in the floppy drive. i.e. Once a system is infected with a boot-sector virus, any non-write-protected disk accessed by this system will become infected.
What is File or Program Viruses
Learn ethical-hacking - ethical-hacking tutorial - virus-program - ethical-hacking examples - ethical-hacking programs
- Affects system program files - Some files/programs, when executed, load the virus in the memory and perform predefined functions to infect the system. They infect program files with extensions like
- .EXE,
- .COM,
- .BIN,
- .DRV and
- .SYS.
What is Multipartite Viruses
- A multipartite virus is a computer virus that infects multiple different target platforms, and remains recursively infective in each target. It attempts to attack both the boot sector and the executable, or programs, files at the same time.
- Attack in two ways : When the virus attaches to the boot sector, it will in turn affect the system's files, and when the virus attaches to the files, it will in turn infect the boot sector.
- Most critical virus : This type of virus can re-infect a system over and over again if all parts of the virus are not eradicated.
- Ghostball was the first multipartite virus, discovered by Fridrik Skulason in October 1989. Other examples are Invader, Flip, etc.
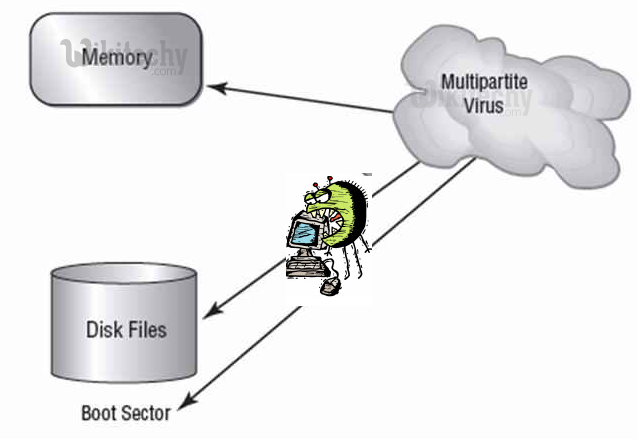
Learn ethical-hacking - ethical-hacking tutorial - multipartite-virus - ethical-hacking examples - ethical-hacking programs
What is Stealth Viruses
- One of the most powerful virus. These viruses are stealthy in nature means it uses various methods for hiding themselves to avoid detection. They sometimes remove themselves from the memory temporarily to avoid detection by antivirus. They are somewhat difficult to detect.
- Reaction for the antivirus scanning - When an antivirus program tries to detect the virus, the stealth virus feeds the antivirus program a clean image of the file or boot sector.
What is Polymorphic Viruses
- Polymorphic viruses have the ability to mutate implying that they change the viral code known as the signature each time they spread or infect.
- Thus an antivirus program which is scanning for specific virus codes unable to detect it's presence.
What is Macro Viruses
- A macro virus is a computer virus that "infects" a Microsoft Word or similar application and causes a sequence of actions to be performed automatically once the application is started or something else triggers it.
- Macro viruses tend to be surprising but relatively harmless.
- A macro virus is often spread as an e-mail virus. Well-known examples are Concept Virus and Melissa Worm.
What is Malware
- Malware is programming or files that are developed for the purpose of doing harm. Thus, malware includes computer viruses, worms, Trojan horses, spyware, hijackers, and certain type of adware.
- This article will focus on those malware that are considered viruses, trojans, worms, and viruses, though this information can be used to remove the other types of malware as well. We will not go into specific details about any one particular infection, but rather provide a broad overview of how these infections can be removed. For the most part these instructions should allow you to remove a good deal of infections, but there are some that need special steps to be removed and these won't be covered under this tutorial.
- Before we continue it is important to understand the generic malware terms that you will be reading about.
What is Backdoor
- A program that allows a remote user to execute commands and tasks on your computer without your permission. These types of programs are typically used to launch attacks on other computers, distribute copyrighted software or media, or hack other computers.
What is Hijackers
- A program that attempts to hijack certain Internet functions like redirecting your start page to the hijacker's own start page, redirecting search queries to a undesired search engine, or replace search results from popular search engines with their own information.
What is Spyware
- A program that monitors your activity or information on your computer and sends that information to a remote computer without your Knowledge.
What is Adware
- A program that generates popups on your computer or displays advertisements. It is important to note that not all adware programs are necessarily considered malware.
- There are many legitimate programs that are given for free that display ads in their programs in order to generate revenue. As long as this information is provided up front then they are generally not considered malware.
What is Dialler
- A program that typically dials a premium rate number that has per minute charges over and above the typical call charge. These calls are with the intent of gaining access to pornographic material.
What is Trojan
- A program that has been designed to appear innocent but has been intentionally designed to cause some malicious activity or to provide a backdoor to your system.
What is Worm
- A program that when run, has the ability to spread to other computers on its own using either mass-mailing techniques to email addresses found on your computer or by using the Internet to infect a remote computer using known security holes.
How To Create A Virus Using C++ Pdf
Source: https://www.wikitechy.com/tutorials/ethical-hacking/virus
Posted by: daviswallard1976.blogspot.com

0 Response to "How To Create A Virus Using C++ Pdf"
Post a Comment